Microsoft Defender for Identity Deep Dive: Part 1
Building on our Defender XDR series, this post focuses specifically on Microsoft Defender for Identity, the primary identity threat detection and response solution for hybrid environments.
Introduction: Protecting the Keys to Your Kingdom
In our previous exploration of Microsoft Defender for Office 365, we examined how organizations can safeguard their email and collaboration environments from sophisticated threats.
Learn more about how Microsoft Defender XDR unifies protection across your entire digital estate here:
Today, we shift our focus to an equally critical and often more vulnerable component of your security infrastructure: Identity.
Identity has become the new perimeter. With the rise of hybrid and cloud environments, traditional network boundaries have dissolved, making user identities the primary target for attackers. A compromised identity is often the gateway to your organization’s most sensitive assets, making identity protection not just important, but mission-critical.
This is where Microsoft Defender for Identity comes into play, your organization’s dedicated Identity Threat Detection and Response (ITDR) solution.
Focus: Microsoft Defender for Identity Deep Dive
In today’s blog, we’ll take a comprehensive look at Microsoft Defender for Identity. While the broader Defender XDR ecosystem provides unified protection across your entire digital estate, Defender for Identity serves as the specialized guardian of your identity infrastructure. As a cloud-based security solution that monitors and protects your on-premises Active Directory and cloud identities, it forms the cornerstone of modern identity security, making it essential to understand in depth.
Understanding Microsoft Defender for Identity
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection- old name) is a cloud-based security solution designed to help your Security Operations teams deliver modern Identity Threat Detection and Response (ITDR) capabilities across hybrid environments. It leverages signals from both on-premises Active Directory and cloud identities to identify, detect, and investigate advanced threats directed at your organization.
Microsoft Defender for Identity Plan
Microsoft Defender for Identity offers a single, unified product and does not come with different Plan 1 or Plan 2 options like some other Defender products. Instead, it is offered as a standalone license or bundled within broader Microsoft suites such as Enterprise Mobility + Security E5 (EMS E5) and select Microsoft 365 E5 subscriptions.
What Makes Identity Protection Critical?
In modern cyberattacks, identity compromise is often the first domino to fall. Attackers typically:
Gain access through a low-privileged account
Move laterally across the network
Escalate privileges systematically
Eventually compromise high-value targets like domain administrators
Achieve domain dominance and access sensitive data
Defender for Identity is specifically designed to detect and disrupt this attack chain at every stage.
The Technology Stack
Microsoft Defender for Identity delivers comprehensive identity protection through four key capabilities:
1. Prevent Breaches
Using proactive identity security posture assessments to identify and remediate vulnerabilities before attackers can exploit them.
2. Detect Threats
Leveraging real-time analytics and threat intelligence to identify sophisticated identity-based attacks as they occur.
3. Investigate Suspicious Activities
Providing clear, actionable incident information that enables rapid investigation and understanding of attack scope.
4. Respond to Attacks
Enabling automatic response capabilities to compromised identities, reducing response times and limiting damage.
The Technology Stack: How Defender for Identity Works
The power of Defender for Identity lies in its sophisticated architecture and technology combination:
Sensor-Based Monitoring
Defender for Identity deploys lightweight sensors directly on your domain controllers, Active Directory Federation Services (AD FS) servers, and Active Directory Certificate Services (AD CS) servers. These sensors monitor and parse network traffic, Windows events, and authentication activities in real-time without requiring any additional infrastructure.
Machine Learning and Behavioral Analytics
Advanced algorithms establish baseline behaviors for users and entities across your environment. By learning normal patterns of authentication, resource access, and privilege usage, Defender for Identity can detect anomalies that indicate potential compromise.
Threat Intelligence Integration
Defender for Identity benefits from Microsoft’s global threat intelligence network, generated by security researchers, threat hunters, and augmented by partner intelligence. This enables the solution to recognize attacker tools, techniques, and procedures (TTPs) aligned with the MITRE ATT&CK framework.
Cloud-Scale Analytics
As a cloud-native solution, Defender for Identity processes vast amounts of identity data without impacting on-premises performance, providing insights that would be impossible with traditional on-premises security tools.
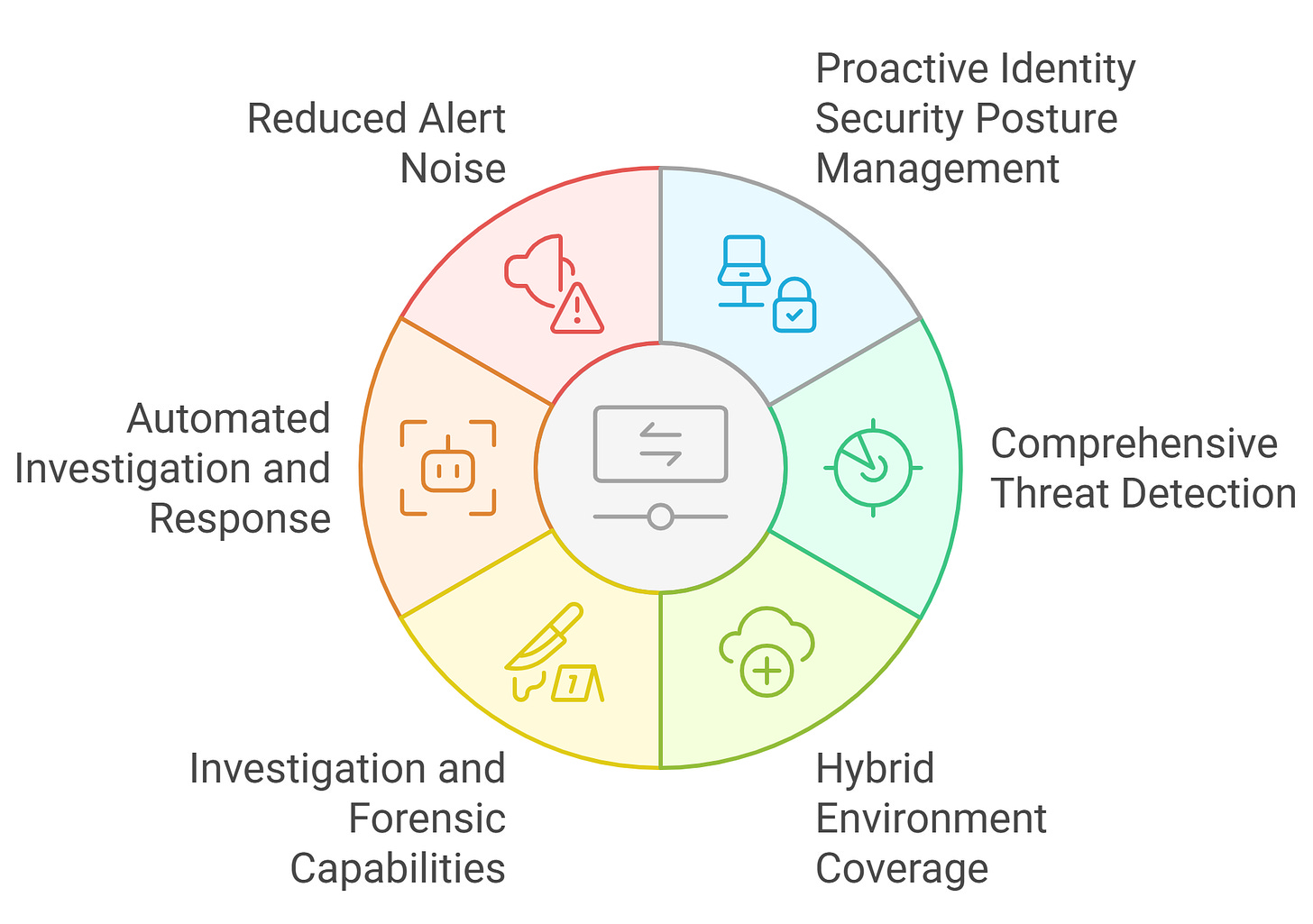
Deep Dive: Core Capabilities
1. Proactive Identity Security Posture Management
Defender for Identity doesn’t just detect threats—it helps you prevent them. Through integration with Microsoft Secure Score, it provides continuous security assessments that help you:
Identify Identity Misconfigurations: Discover weak security settings, overly permissive access rights, and policy gaps that create opportunities for attackers.
Understand Lateral Movement Paths: Visualize exactly how an attacker could move laterally through your organization to reach sensitive accounts. This critical capability shows potential attack paths before they’re exploited.
Receive Actionable Recommendations: Get specific, prioritized guidance on how to reduce your identity attack surface and implement security best practices.
2. Comprehensive Threat Detection Across the Cyber-Attack Kill Chain
Defender for Identity identifies advanced threats across every stage of an attack:
Reconnaissance Phase
Detects when attackers attempt to gather information about your environment:
Account enumeration attempts
Network scanning for domain controllers
DNS reconnaissance
Directory service queries
Compromised Credentials
Identifies credential theft and misuse attempts:
Brute force attacks
Password spray campaigns
Suspicious authentication patterns
Failed authentication anomalies
Honey Token account access
Lateral Movement
Catches attackers attempting to move through your network:
Pass-the-Hash attacks
Pass-the-Ticket attacks
Overpass-the-Hash techniques
Remote execution attempts
SMB session enumeration
Domain Dominance
Alerts on activities indicating attackers have achieved high-level control:
Golden Ticket attacks (Kerberos ticket forging)
Silver Ticket attacks
Skeleton Key malware deployment
DCSync attacks (malicious domain replication)
DCShadow attacks (rogue domain controller registration)
Remote code execution on domain controllers
3. Hybrid Environment Coverage
Modern organizations operate in hybrid environments, and Defender for Identity provides seamless protection across both:
On-Premises Active Directory: Full monitoring of domain controllers, including authentication events, privilege changes, and administrative activities.
Active Directory Federation Services (AD FS): Protection for federated identity infrastructure, detecting compromise attempts against your federation servers.
Active Directory Certificate Services (AD CS): Monitoring of certificate authority activities to detect certificate-based attacks.
Cloud Identity Integration: Correlation with Azure Active Directory (Entra ID) signals for complete visibility across your identity landscape.
4. Investigation and Forensic Capabilities
When security alerts fire, time is critical. Defender for Identity provides security analysts with powerful investigation tools:
Unified Incident Timeline: View the complete attack story in chronological order, understanding how an incident evolved and which assets were impacted.
Entity Profiling: Deep dive into user and device profiles, examining authentication patterns, group memberships, accessed resources, and historical activities.
Alert Correlation: Automatically correlate related security alerts into comprehensive incidents, reducing alert fatigue and providing context.
Evidence Collection: Access detailed evidence including network traffic captures, event logs, and authentication data to support investigations.
5. Automated Investigation and Response (AIR)
Manual incident response is too slow for modern threats. Defender for Identity includes automated response capabilities:
Automatic User Containment: Immediately disable or isolate compromised accounts to prevent further damage.
Playbook-Based Response: Execute pre-defined response actions automatically when specific threat patterns are detected.
Integration with Microsoft Defender XDR: Coordinate response actions across endpoints, email, and identity for comprehensive threat containment.
6. Reduced Alert Noise with Intelligent Prioritization
Not all security alerts deserve equal attention. Defender for Identity reduces alert fatigue through:
Risk-Based Scoring: Prioritizes alerts based on severity, potential impact, and the sensitivity of affected assets.
Context-Aware Alerting: Considers user behavior patterns, organizational context, and threat intelligence before generating alerts.
True Positive Learning: Uses machine learning to continuously improve detection accuracy and reduce false positives.
Integration Ecosystem: The Power of Unity
Microsoft Defender for Identity is not just a standalone security tool, it’s a core pillar of the broader Microsoft Defender XDR ecosystem. Its real strength comes from deep integration with other Microsoft security solutions, forming a unified security fabric where each component reinforces the others, delivering defense capabilities far greater than the sum of their parts.
Conclusion
Microsoft Defender for Identity represents the foundation of modern Identity Threat Detection and Response (ITDR), combining behavioral analytics, machine learning, and global threat intelligence to protect organizations against sophisticated identity-based attacks. From proactive security posture assessments to real-time threat detection and automated response, Defender for Identity provides comprehensive protection across the entire identity attack lifecycle.
The platform’s strength lies in its ability to see what others miss, detecting subtle behavioral anomalies and attack techniques that traditional security tools overlook. By monitoring authentication patterns, privilege usage, and lateral movement attempts across hybrid environments, Defender for Identity serves as an always-vigilant guardian of your most critical security boundary: identity.
As cybercriminals increasingly target identities as the primary attack vector, understanding the deep technical capabilities of Defender for Identity becomes essential for security professionals. This foundation knowledge prepares you to implement robust identity security defenses and respond effectively when identity-based attacks occur.
In a world where identity is the new perimeter, Microsoft Defender for Identity ensures that perimeter is well-defended.
Ready to expand your security coverage beyond identity? Our next post will explore Microsoft Defender for Cloud Apps, examining how it protects your cloud applications and helps you gain visibility and control over your SaaS environment.